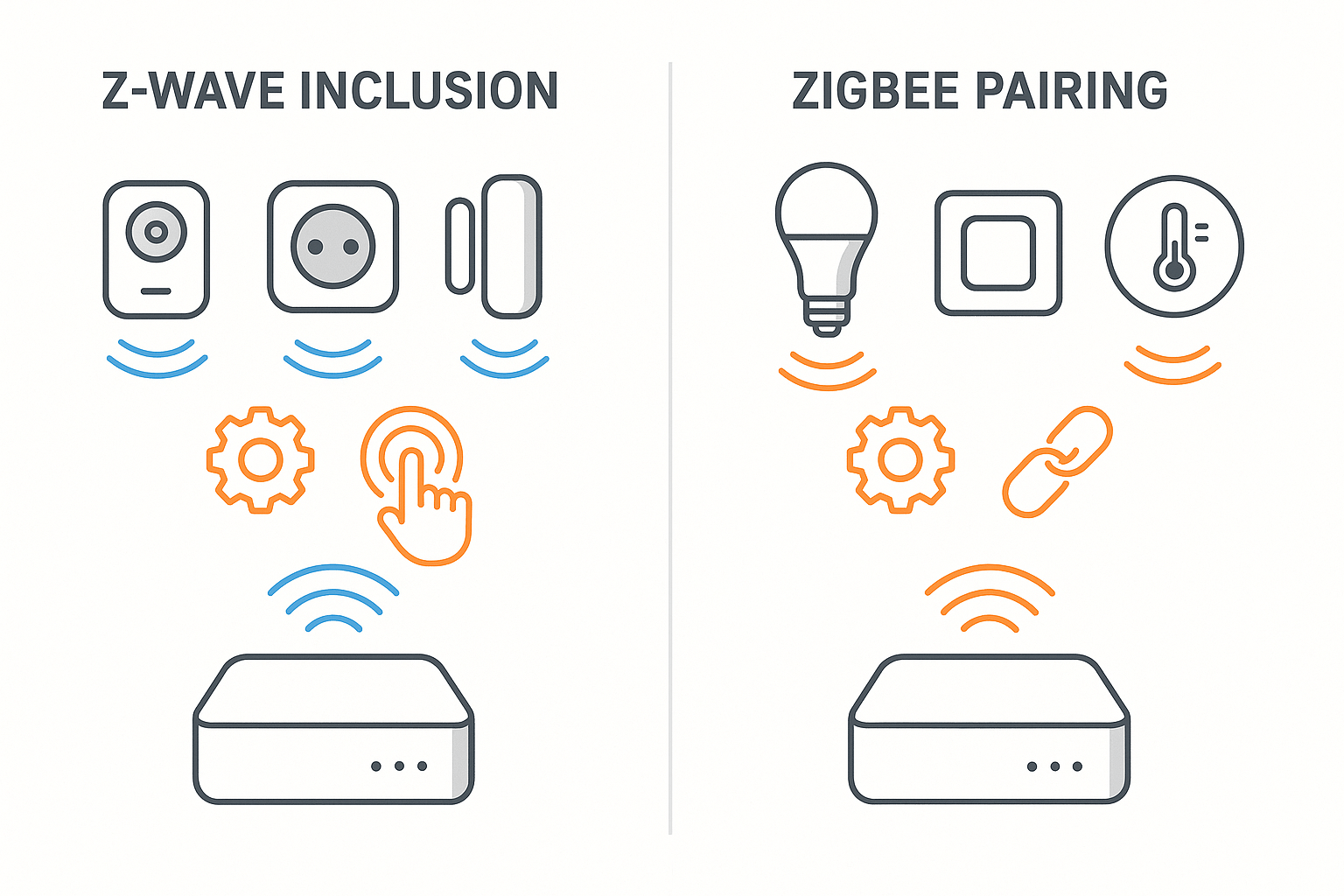
Understanding the fundamental differences between Z-Wave inclusion and Zigbee pairing processes is essential for successful smart home device setup and network management. While both protocols achieve the same goal of adding devices to a network, they use different terminologies, procedures, and security mechanisms. This comprehensive guide explains the technical details, practical procedures, and troubleshooting approaches for both protocols.
1. Understanding Network Joining Fundamentals
Both Z-Wave and Zigbee protocols require devices to join a network before they can communicate with other devices or be controlled by a central hub. However, the terminology, procedures, and underlying mechanisms differ significantly between the two protocols.
Terminology and Process Names
The different terms used by each protocol reflect their distinct approaches to network formation and device commissioning.
Z-Wave "Inclusion": The formal Z-Wave term for adding a device to a network is "inclusion." This terminology reflects the centralized nature of Z-Wave networks where devices are explicitly included into an existing network structure managed by a primary controller.
Zigbee "Pairing" or "Joining": Zigbee uses "pairing" as a consumer-friendly term, though the formal technical term is "joining." Both refer to the same process of commissioning a device onto a Zigbee network. The pairing terminology has become popular because it's more intuitive for consumers familiar with Bluetooth pairing.
Protocol Architecture Differences
The fundamental differences in how Z-Wave and Zigbee networks are structured directly impact how devices join these networks.
Z-Wave Network Structure: Modern Z-Wave networks support multiple controllers, but typically have one primary controller that manages network operations and maintains the master copy of network topology. Z-Wave Plus networks can include secondary controllers and support advanced features like Network Wide Inclusion (NWI), where any controller can add devices that become available throughout the network.
Zigbee Network Structure: Zigbee networks have one coordinator device that forms and manages the network, but multiple router devices can facilitate the joining process for new devices. The coordinator maintains network security and policies, while routers extend coverage and help with device commissioning. End devices rely on routers or the coordinator for network connectivity.
Network Size Limits: Classic Z-Wave networks support up to 232 devices with node IDs 1-232, while Z-Wave Long Range can theoretically support thousands of devices. Zigbee networks can support much larger numbers of devices (theoretically 65,000+ per network) using complex addressing schemes.
Addressing Systems: Z-Wave uses simple numeric node IDs assigned sequentially by the primary controller. Zigbee uses more complex addressing with 64-bit extended addresses (IEEE addresses) for permanent device identification and 16-bit network addresses for routing that can change as the network evolves.
2. Z-Wave Inclusion Process Deep Dive
The Z-Wave inclusion process is a well-defined procedure that establishes communication between a new device and the existing network. Understanding the technical details helps with troubleshooting and optimising the setup process.
Modern Z-Wave Inclusion Procedures
Z-Wave inclusion has evolved to include more sophisticated security and convenience features while maintaining the straightforward process that made Z-Wave popular.
Controller Preparation: The primary controller must be put into inclusion mode, which opens a time window (typically 30-60 seconds) during which new devices can be added. Modern controllers often provide visual and audio feedback during this process and may support extended inclusion modes for difficult installations.
Device Activation: The device to be included must be activated using its specific inclusion method. This varies by device type but commonly involves pressing a button, power cycling, or following a specific sequence of actions. Modern devices often provide LED feedback to indicate inclusion status.
Discovery and Negotiation: The controller discovers the new device and begins a negotiation process to determine the device's capabilities, supported command classes, and security requirements. This information determines how the device integrates into the network and what features are available.
Node ID Assignment: The controller assigns a unique node ID to the new device. This ID is used for all future communications and routing decisions. The assignment is permanent until the device is excluded from the network or the network is reset.
Network Wide Inclusion (NWI): In modern Z-Wave Plus networks, devices included by any controller become available to all controllers in the network automatically. This simplifies multi-controller installations and improves network flexibility.
Z-Wave Security Framework Evolution
Z-Wave security has evolved significantly from basic encryption to sophisticated multi-level security frameworks.
Legacy Non-Secure Inclusion: Traditional Z-Wave inclusion occurs without encryption, making the process fast and simple but potentially vulnerable to eavesdropping. Non-secure devices can participate in basic network functions but cannot access secure command classes.
S0 Security (Legacy Secure): Z-Wave S0 security provides encrypted communication using a shared network key. Secure inclusion requires additional steps including key exchange and authentication. S0 is considered legacy but remains widely supported for backward compatibility.
S2 Security Framework: Z-Wave S2 introduces multiple security levels including S2 Unauthenticated, S2 Authenticated, and S2 Access Control. Each level provides different security guarantees and may require different setup procedures including QR code scanning or manual key entry.
SmartStart Technology: SmartStart allows devices to be pre-configured with network information using QR codes before physical installation. Devices can automatically join the network when powered on, simplifying installation while maintaining security through pre-shared keys.
3. Zigbee Pairing Process Deep Dive
Zigbee pairing involves a more complex process due to the protocol's distributed architecture and advanced security features. Understanding these complexities is essential for successful device setup and network management.
Zigbee Network Formation and Joining
The Zigbee joining process involves multiple phases and can follow different paths depending on the device type and network configuration.
Network Discovery: Devices seeking to join a Zigbee network first scan for available networks by listening for beacon frames transmitted by the coordinator and routers. These beacons contain network information including the network identifier (PAN ID) and whether the network is open for joining.
Association Process: Once a suitable network is found, the device sends an association request to the coordinator or a router. The network device evaluates the request based on network capacity, security policies, and device capabilities, then may accept or reject the joining attempt.
Authentication and Key Exchange: Accepted devices undergo authentication and security key exchange. This process varies depending on the Zigbee version and security configuration but typically involves multiple rounds of cryptographic operations to establish secure communication.
Network Address Assignment: Successfully authenticated devices receive a 16-bit network address used for routing within the network. This address is dynamically assigned and may change if the device moves or the network topology changes significantly.
Service Discovery: After joining, devices typically undergo service discovery where they announce their capabilities and discover available services on the network. This process enables proper integration with smart home hubs and other network devices.
Zigbee 3.0 Enhanced Security and Commissioning
Zigbee 3.0 introduces significant security enhancements that affect the pairing process and overall network security.
Install Codes and Security: Zigbee 3.0 devices typically use install codes, which are unique cryptographic keys pre-installed during manufacturing. These codes ensure that only authorised devices can join the network and prevent unauthorised access during the pairing process.
Centralised Security Management: Unlike earlier Zigbee versions, Zigbee 3.0 uses a centralised security model where the coordinator manages all security keys and policies. This simplifies security management while providing stronger protection against various attack vectors.
Secure Commissioning Process: The commissioning process in Zigbee 3.0 includes multiple security checks and key exchanges to ensure that devices are properly authenticated and configured. This process provides significantly better security than earlier versions but may take longer to complete.
Special Zigbee Device Types
Different Zigbee device types have different joining procedures and requirements.
Green Power Devices: Zigbee Green Power devices use a different joining mechanism designed for ultra-low-power operation. These devices can join networks without traditional pairing procedures and often use energy harvesting rather than batteries.
Sleepy End Devices: Battery-powered devices that spend most of their time in sleep mode require special consideration during joining to ensure they can complete the process before entering sleep mode.
4. Comparative Analysis: Modern Setup Experience
Understanding the practical differences between Z-Wave inclusion and Zigbee pairing helps in choosing the right protocol and managing user expectations during device setup.
Setup Time and User Experience
The actual user experience of device setup has converged significantly between protocols, though some differences remain.
Typical Setup Duration: Modern Z-Wave inclusion typically completes within 10-30 seconds for basic devices, with S2 secure inclusion taking 30-60 seconds. Zigbee pairing generally takes 15-45 seconds for most devices, with secure Zigbee 3.0 devices occasionally requiring up to 2 minutes for complex security setup.
User Interaction Requirements: Both protocols now support simplified setup procedures. Z-Wave typically requires a button press or power cycle, while Zigbee may use similar methods or QR code scanning for devices with install codes.
Setup Feedback: Modern Z-Wave controllers provide immediate and clear feedback about inclusion success or failure. Contemporary Zigbee implementations (such as SmartThings, Home Assistant with ZHA/Zigbee2MQTT) now provide real-time feedback that's comparable to Z-Wave systems, though historically Zigbee provided less immediate feedback.
Security Implementation Comparison
Both protocols have evolved to provide strong security, but with different approaches and default settings.
Default Security Posture: Zigbee 3.0 includes security by default with mandatory encryption and authentication. Z-Wave still allows both secure and non-secure inclusion, providing flexibility for different security requirements but requiring conscious security decisions.
Key Management Complexity: Zigbee 3.0 uses device-specific install codes that provide strong security with minimal user interaction. Z-Wave S2 uses QR codes or manual key entry for high-security devices, which can be more complex but provides clear security control.
Security Verification: Both protocols provide methods to verify that devices have joined securely, but the specific procedures and feedback mechanisms differ between implementations.
5. Advanced Setup Procedures and Optimisation
Successful device setup goes beyond basic inclusion or pairing procedures. Advanced techniques and best practices can improve success rates and reduce troubleshooting time.
Pre-Setup Planning and Network Assessment
Proper planning before beginning device setup can prevent many common issues and improve the overall experience.
Network Health Check: Before adding new devices, assess the current network status including device count, signal strength, and any existing connectivity issues. Use network diagnostic tools provided by your hub to identify potential problems.
Device Compatibility Verification: Verify that new devices are compatible with your existing network, including protocol version, security requirements, and any manufacturer-specific considerations. Check for firmware updates that may be required for optimal operation.
Physical Environment Assessment: Consider the physical environment including signal obstacles, interference sources, and the planned final location of the device. Plan temporary placement strategies for setup if needed.
Optimal Setup Procedures
Following optimised procedures can improve setup success rates and reduce the time required for device commissioning.
Proximity Setup Strategy: Perform initial device setup close to the hub or coordinator to ensure strong signal strength during the joining process. This is particularly important for battery-powered devices that may have lower transmit power.
Sequential Device Addition: Add devices one at a time rather than attempting multiple simultaneous setups. This reduces network congestion and makes troubleshooting easier if problems occur.
Power and Battery Considerations: Ensure that battery-powered devices have fresh batteries during setup. Low battery levels can cause setup failures or incomplete configuration. For mains-powered devices, verify stable power supply.
Network Refresh Procedures: After adding multiple devices, perform network optimisation or refresh procedures as recommended by your hub manufacturer to ensure optimal routing and performance.
6. Troubleshooting Common Setup Issues
Understanding common setup problems and their solutions can significantly reduce the time and frustration associated with device commissioning.
Device Reset and Factory Restoration
When devices fail to join properly, factory reset procedures are often necessary to clear previous network information.
Z-Wave Exclusion Process: Z-Wave devices should be excluded from their previous network before inclusion in a new network. Most Z-Wave controllers support "general exclusion" that can remove devices regardless of their original network.
Zigbee Factory Reset Methods: Zigbee devices typically require specific factory reset procedures that vary by manufacturer. Common methods include holding buttons for specific durations, power cycling sequences, or using manufacturer-specific tools.
Security Key Clearing: Devices that have been securely included in other networks may need security key clearing before they can join new networks. This often requires specific reset procedures beyond basic factory reset.
Signal Strength and Network Issues
Poor signal strength remains one of the most common causes of setup failures in both Z-Wave and Zigbee networks.
Diagnostic Tools: Use your hub's diagnostic tools to measure signal strength and identify potential connectivity issues. Many modern hubs provide real-time signal strength indicators and network topology views.
Range Extension Strategies: If devices cannot join due to range limitations, consider adding repeater devices, repositioning the hub, or using high-power inclusion modes if available.
Interference Identification: Identify potential interference sources including Wi-Fi networks, Bluetooth devices, and other wireless systems. Use spectrum analysis tools if available to identify specific interference patterns.
Security and Authentication Failures
Security-related setup failures are becoming more common as protocols implement stronger security measures.
Install Code and QR Code Issues: Verify that install codes or QR codes are correctly entered and that they match the device. Some codes may be difficult to read due to printing quality or placement.
Security Level Mismatches: Ensure that the device supports the security level required by your network and that the hub is configured to accept the device's security capabilities.
Time-Sensitive Security Procedures: Some security procedures are time-sensitive. Ensure that all steps are completed within the required timeframes and restart the process if timeouts occur.
7. Network Management and Post-Setup Optimisation
Successful device setup is just the beginning. Proper network management and optimisation ensure long-term reliability and performance.
Network Topology Optimisation
Both Z-Wave and Zigbee networks benefit from periodic optimisation to ensure optimal routing and performance.
Z-Wave Network Healing: Z-Wave networks should be "healed" periodically to update routing tables and optimise communication paths. This process rediscovers the network topology and updates routing information in all devices.
Zigbee Network Maintenance: Zigbee networks are generally self-optimising, but manual optimisation may be beneficial after adding many devices or making significant changes to the physical environment.
Performance Monitoring: Regularly monitor network performance including response times, battery levels, and communication reliability. Address issues promptly to prevent cascade failures.
Security Verification and Maintenance
Regular security verification ensures that devices remain properly secured and that security features are functioning correctly.
Encryption Status Verification: Verify that devices are using encryption for sensitive communications and that security features are active and properly configured.
Security Key Management: Maintain proper security key management including periodic key rotation if supported and securing key information appropriately.
Device Authentication Monitoring: Monitor device authentication status and address any devices that show authentication issues or security warnings.
8. Future Developments and Industry Trends
The landscape of device setup and network joining continues to evolve with new technologies and standards that promise to improve security, usability, and interoperability.
Matter Integration and Bridging
The Matter standard is changing how different protocols interact and how devices are commissioned across different ecosystems.
Matter Bridging Approach: Matter currently works through hub-based bridging rather than directly unifying Z-Wave and Zigbee protocols. Hubs like SmartThings or Home Assistant can bridge Z-Wave and Zigbee devices into a Matter fabric, providing unified control while maintaining the underlying protocol benefits.
Simplified Commissioning: Matter aims to provide consistent commissioning procedures across different device types and protocols, potentially reducing user confusion and training requirements.
Enhanced Interoperability: While Matter doesn't eliminate protocol differences, it provides a common application layer that can simplify device interaction and automation across different underlying technologies.
Enhanced Security and Authentication
Future developments in security technology will continue to improve the security of device setup and network communications.
Advanced Cryptographic Methods: New cryptographic techniques including post-quantum cryptography may be implemented to provide long-term security against emerging threats.
Hardware Security Integration: Hardware security modules and trusted execution environments may become more common in smart home devices, providing stronger protection for security keys and authentication procedures.
Biometric and Multi-Factor Authentication: Advanced authentication methods may be integrated into device setup procedures to provide stronger user verification and device authorisation.
User Experience Evolution
Ongoing developments focus on further simplifying the user experience while maintaining or improving security.
Automatic Device Discovery: Future systems may provide more sophisticated automatic device discovery and setup with minimal user intervention required.
AI-Assisted Setup: Artificial intelligence may be used to optimise device placement, predict setup issues, and provide intelligent troubleshooting guidance.
Visual and Augmented Reality Guidance: AR applications may provide visual guidance for device installation and setup, helping users optimise placement and configuration.